Day Six: File Permissions and Access Control Lists - The #90DaysOfDevOps Challenge
Welcome to Day 6 of the #90DaysOfDevOps challenge! Today, we discuss more about file permissions and access control lists. We discussed this topic further in the day 3 post. Every file and directory in a Linux system is associated with a set of permissions that determine who can read, write, or execute them. On the other hand, ACLs offer more advanced control over file permissions, allowing for more fine-grained access management. Two crucial topics in DevOps.
We will be using a linux virtual machine for the tasks today.
The Basics of Linux File Permissions
Linux file permissions are organized into three categories, each with its own set of permissions:
Owner: The user who owns the file or directory. The owner has the most control over the file, including the ability to change its permissions.
Group: A collection of users who share certain permissions to the file. The group permissions allow specified members to access the file.
Others: Any user who does not fall into the owner or group categories. These are typically users who are not directly associated with the file or directory.
Types Of Permissions
The basic types of permissions that can be assigned to each of the categories mentioned above are:
r: Read - Allows the user to view the contents of the file or directory.w: Write - Allows the user the ability to modify the contents of the file or directory, including creating, deleting, or renaming it.x: Execute - Permits the user to execute the file if it is a program or script. For directories, it allows the user to access its contents.-: No permissions.
Modifying File Permissions
In Linux, the chmod command is used to modify file permissions. It can be used in various ways to set permissions for the owner, group, and others, either explicitly or implicitly.
Using the Numeric Mode
One common method is to use the numeric mode, where a three-digit octal number represents the permissions for the owner, group, and others, respectively. Each digit corresponds to a sum of read (r), write (w), and execute (x) permissions.
Read (r): 4
Write (w): 2
Execute (x): 1
For Example:
chmod 700 file.txt - Owner has read, write, and execute permissions (4+2+1 = 7); group(0+0+0 = 0) and others(0+0+0 = 0) have no permissions
Tip: You can think of it as a table when setting permissions for the different categories.
| Owner | Group | Others |
| 7 | 0 | 0 |
Using Symbolic Mode
Another method is to use symbolic mode, where you explicitly specify the permissions to add (+), remove (-), or set (=) for the owner (u), group (g), or others (o).
For example:
chmod u+r file.txt # Add read permission for the owner
chmod g-w file.txt # Remove write permission for the group
chmod o+x file.txt # Add execute permission for others
Additionally, you can combine multiple symbols and permissions in a single command, providing more flexibility in modifying permissions.
chmod u+r,g-w,o+x file.txt # Add read permission for the owner, remove write permission for the group, add execute permission for others
chmod u=rwx,g=r,o= file.txt # Set read, write, and execute permissions for the owner, read permission for the group, remove all permissions for others
Changing Ownership and Group
Apart from modifying permissions, it's also possible to change the ownership and group of a file or directory using the chown and chgrp commands.
chown user:group file.txt # Change the owner and group of the file
Here, user represents the new owner, and group represents the new group.
Tip: To get information about a files owner and group you can use the command ls -l or stat
Advanced Permissions with ACL
While traditional Unix file permissions provide basic control over access to files and directories, Access Control Lists (ACLs) offer more control. ACLs allow specifying permissions for individual users or groups beyond the standard owner, group, and others.
The getfacl command is used to view ACLs for a file or directory:
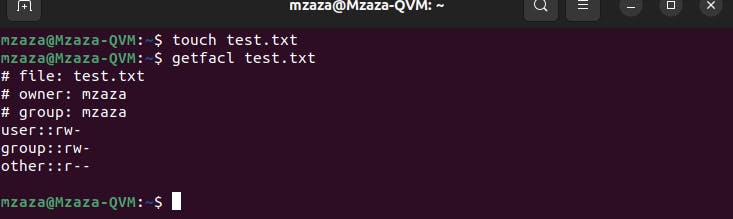
To modify ACLs, the setfacl command is used:

To remove an ACL entry for a user we use setfacl like so:
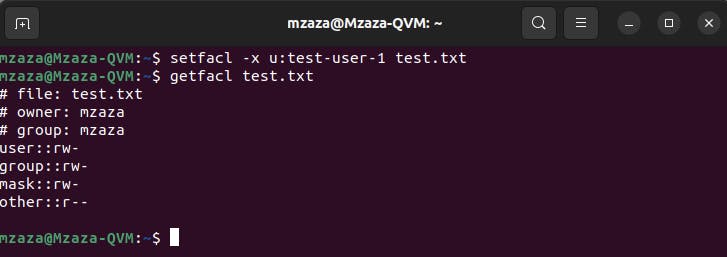
By using ACLs, administrators can define more precise permissions tailored to the specific needs of users or groups, enhancing the security and flexibility of file access control.
That concludes our journey for Day 6 of the #90DaysOfDevOps challenge. Today, we explored more about file permissions and introduced access control lists. Both play a crucial role in ensuring the security and integrity of systems and are frequently used, as we saw on Day 3. Stay tuned for more exciting challenges and insights as we continue our DevOps journey together.

